Hey guys, i am back again with another article, and today i want to touch a bit on Kenya’s Cybersecurity issue. Most of us have heard the NEWS, Kenya has a major cybersecurity issue.
Kenya has the highest internet penetration in Africa with over 31 million people having access to the internet, according to a report by Jumia Business Intelligence and GSMA Mobile.
With more and more Kenyans being able to access the internet from mobile devices like smartphones and tablets, also comes the rise of mobile money transactions, access to loans and economic prosperity for the country.
NOTE:
The country has only 1,700 certified cybercrime professionals, too few to secure the Kenyan population of close to 50 million against cyber-attacks on the rise.
Some 10.2 million threats were detected in the last three months of 2018, over 2,200 times the 4,589 recorded in the same period the previous year.
President Uhuru Kenyatta last week launched the country’s Digital Economy Blueprint at the Transform Africa Summit in Kigali, Rwanda, the first in Africa.

But with the acceleration of digitization comes insecure consumer habits and easy targets. This coupled with a lack of coherent legislation and regulatory frameworks, as well as inadequate cybersecurity measures in key sectors, is turning Kenya into a lucrative target for cyber criminals aka Hackers.
As digital consumers, we use the internet every day in order to access social media, do personal or business banking, book a holiday, and get the latest updates on news and sporting events. We perform so many tasks using the internet, believing that it is safe, that we tend to neglect the security and preventative measures to lock out phishing scams and cyber criminals.
The country has been targeted by hackers in several major attacks over the past couple of years, and in 2017 Kenya lost approximately Sh21.2 billion to hackers alone. Should i include the scams, stolen money, fake projects, no i will not.
Kenya is facing a potentially huge cyber-insecurity problem with at least 3000 successful or failed attacks recorded every month.
Now it should be noted that hackers read newspapers. And Kenya has a big ol target on it’s back. Now hackers love targets.
Last year the infamous ransomware attack WannaCrypt hit the NHS and other systems around the world, bringing down critical services. It impacted over 230,000 computers and to this day constitutes one of the largest ever cyber-attacks. According to Microsoft’s latest Security Intelligence Report, ransomware continues to be a popular method used by cybercriminals to solicit money from victims.
At least 19 companies in Kenya were been hit by the WannaCrypt attack. Most of the devices affected were surprisingly Windows XP, Vista and 7.
Vista? XP? Come on Kenya, we can do better than that.
Let’s not forget that the most affected were Governments, Hospitals, Financial Institutions, Homes, Universities and colleges.
I believe i may have a solution. But before i get into that, i would like to list down some of the common attacks that Kenyans fall into. But first
What is Cybercrime? It is as any offense that is committed using a computer, network or hardware device. It is not a new occurrence, but its scope is constantly evolving. Once cyber criminals have your personal details, they gain access to an abundance of information that will allow them to clone just about any account that is tied to you. This includes: credit cards, investment bonds, personal savings accounts, as well as cheque accounts. The list does not stop there as your entire identity can be stolen within seconds. Definition by tech company, Symantec.
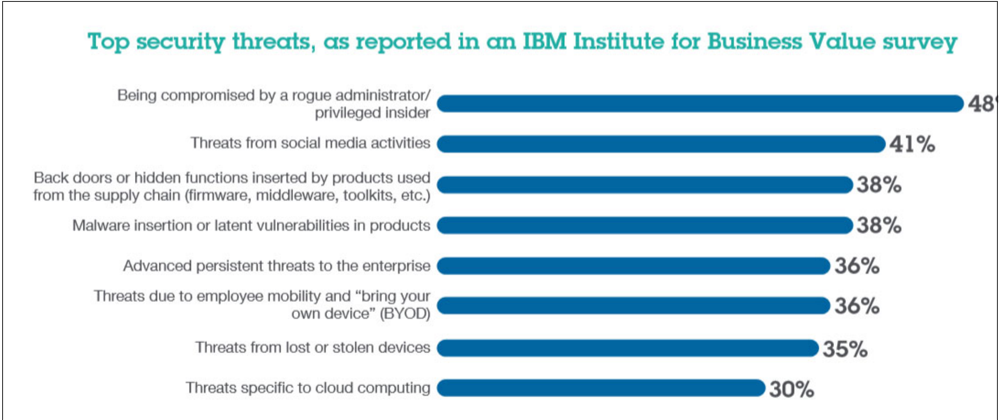
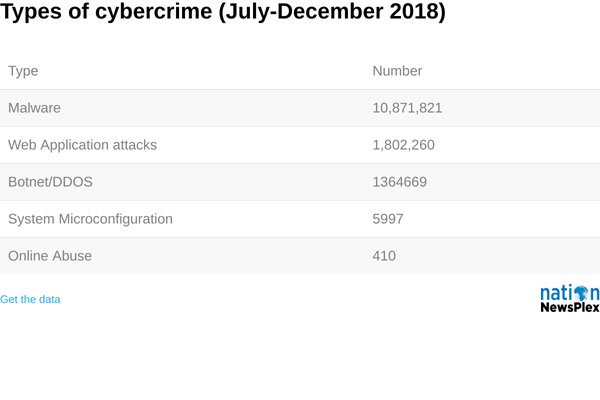
Hacking Techniques
- Social Engineering – This invokes taking advantage of the human beings emotions, psychology and habits.
Social engineering is the art of manipulating people so they give up confidential information. The types of information these criminals are seeking can vary, but when individuals are targeted the criminals are usually trying to trick you into giving them your passwords or bank information, or access your computer to secretly install malicious software–that will give them access to your passwords and bank information as well as giving them control over your computer.
Criminals use social engineering tactics because it is usually easier to exploit your natural inclination to trust than it is to discover ways to hack your software. For example, it is much easier to fool someone into giving you their password than it is for you to try hacking their password (unless the password is really weak).
The weakest link in an organization is not their computers but their employees.
Types of attacks: Phishing, Pretexting and Baiting.
Some of the ways this is used in Kenya is eg. Those messages you get telling you you have won. This is applicable to Emails as well. I’ll mention the preventive measures below this section. - DoS and DDoS Attacks(Distributed/Denial of Service) – This method is one of the most common hacking techniques used by both novice and sophisticated hackers. In this hacking technique, the hacker loads the server with unnecessary traffic leading to Denial of Service (DoS) for authentic users.
The hacker may deploy DDoS attack by using artificial tools like dummy computers or bots to continue launching the server with fake requests to overload it. It leads to the attacked website or webpage unavailable for “real users.” - Keylogging – Keylogging is a hacking technique where the malicious hacker deploys a software called keylogger on your system.
This software records every keystroke and stores the information in a log file which the hacker can look into for sniffing sensitive information like your username and passwords for online accounts.
It is a dangerous hack that can cause identity theft and bank frauds. - Cookie Stealer – Cookies on your browser offer great ease with quick access to frequent sites.
The main idea behind cookies is that they store your personal information including username, password and the site information you visit.Once the hacker steals cookies from your browser, they can even authenticate themselves as you and log in to your online accounts like Facebook, twitter, etc.
Another noteworthy thing is how cookies theft has also become more comfortable.
With the sophisticated algorithms and software, a hacker can download the software, and within few clicks, they will have all your details in front of them. - Bait and Switch – An ancient and conventional technique used by the hackers is bait and switch. The hackers ask the user (victim) to download or run software or an app on their system that seems non-malicious, but there is inbuilt spam or malicious software.
In simple words, they may use free software as bait, and once you click, they’ll switch you onto the malicious link that will put your data at risk.
These are but a few there are more than 300 hacking techniques in the world today. And that number is rapidly increasing. Hackers are coming up with advanced techniques.

Possible Fix For Kenya and other countries
According to Kaspersky, Algeria is leading in Africa in terms of cybercrime and web threats ahead of Egypt, South Africa and Kenya. Why not copy and implement.
I believe we need a dedicated team of cyber “police”. Ordinary police can’t solve cyber crimes. We need a team of ethical hackers and info/cybersecurity pros. All we really need is to train people and of course hire those who are already skilled. Just think about how we would reduce the jobless and these cybersecurity issues. Not only that but this could put us on the map. We would be able to outsource our team to help other countries. This could stack up some revenue.
And after all send a thief to catch a thief?
Send a hacker to catch hackers, right ?
Kenya needs about 10,000 skilled cybersecurity professionals for a start. And an official cybersecurity division.
At the end of the day, these are just the thoughts of one man. Ajulu’s Thoughts 😎. History has proved to us, one man cannot change the world. So share this post and let us change the world! *some theme song should have been played here*
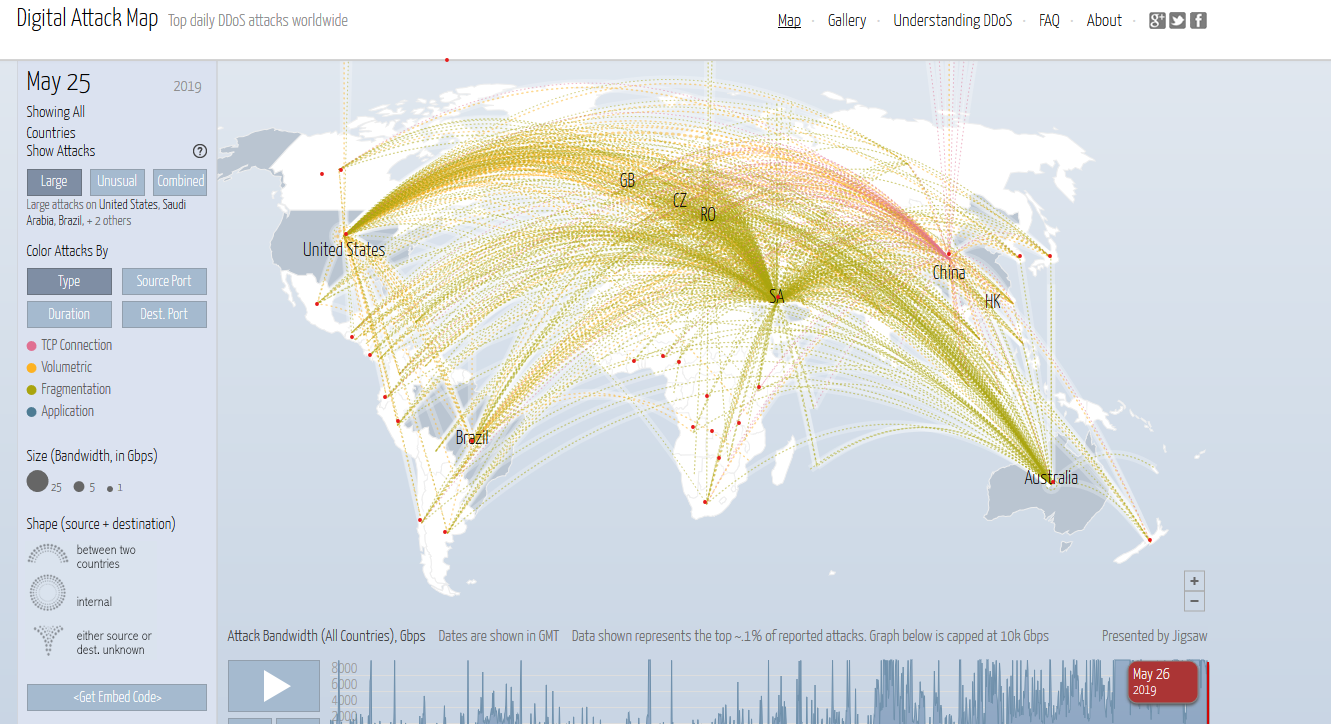
ORGANIZATIONS
It’s important that organizations and their employees across Kenya are aware of the latest threats and how best to protect against them.
Train your people on the basics. Bring in white hackers to help conduct a drill. Hire hackers and let them attempt to hack, report and patch vulnerabilities. Setup honey pots. This can really improve the organization’s security.
The past year has shown us the significant impact of botnet infections on computers worldwide. We’ve seen cybercriminals leveraging less sophisticated methods to infect machines and extort ransoms from victims; and we’ve continued to encounter ransomware in a wide range of cybercrime activity.
Organizations in Kenya that act quickly to adopt security solutions, implement incident response plans and employ the right mix of people will minimize damage and impact from cyber-attacks now and in the future.
Use an email security solution that scans suspicious email attachments and ideally protects at the time a user clicks on an attachment. Antivirus software should help detect and block the download and installation of some ransomware but to mitigate against the impact of sophisticated ransomware, additional protection is required. Advanced threat protection that applies machine learning and artificial intelligence technologies can help.
Be sure to create destruction-resistant backups of critical systems and data. Also, be sure to regularly test that backups are working.
To minimize entry points for ransomware, be sure to keep all software updated, including operating systems, web browsers, plug-ins and security software. Also prioritize patching new releases to enable stronger protection against vulnerabilities.
I would suggest you follow an Instagram Page that goes by the name: Bait and Phish
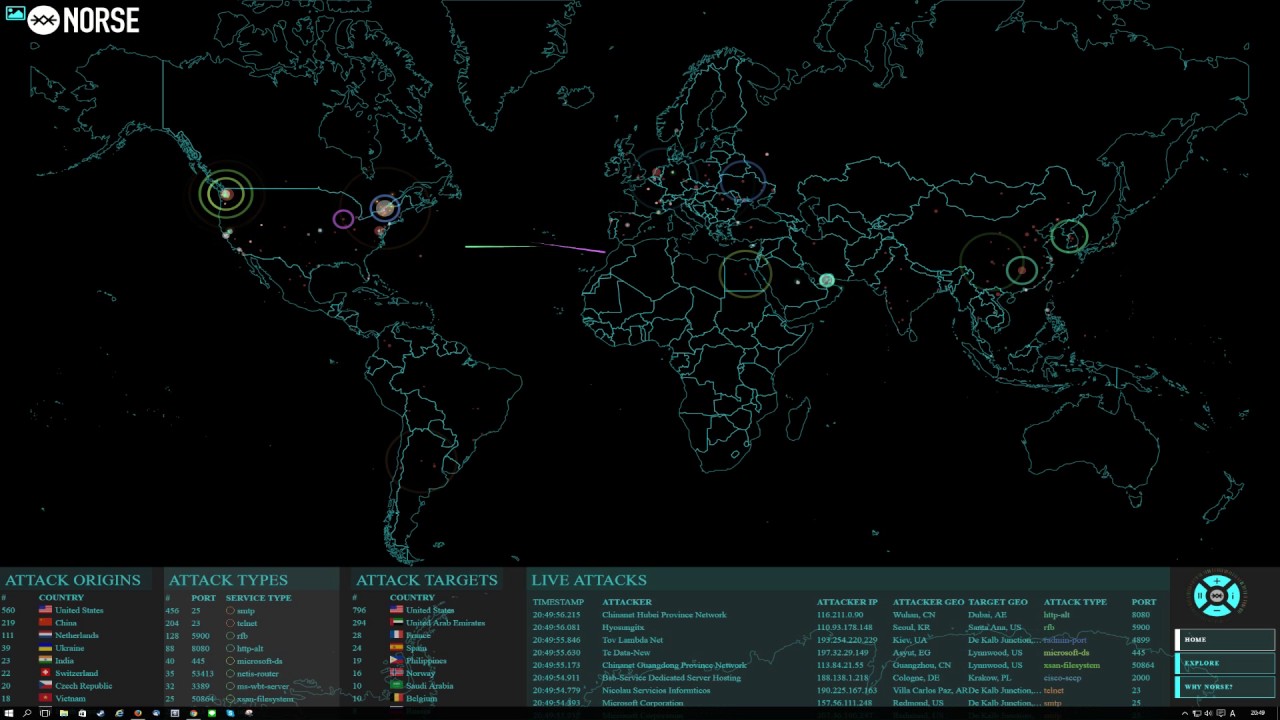
Consumers and Regular Internet Users
- Update your softwares including the Operating System(Android, Windows, Linux regularly
- Avoid clicking on links and downloading things from people you don’t know
- Switch to Linux(Optional) It is indeed true that linux is one of the toughest OS’s. They are not necessarily immune. But in the world in terms of infection Windows is no 1, Mac no 2, Android no 3, All other “oses” no 4, Linux no 5.
- Backup your data REGULARLY
- Do not install cracked software
- Download Softwares from trusted sites e.g their official website or try Ninite
- Be social media savvy – Make sure your social networking profiles (e.g. Facebook, Twitter, YouTube, MSN, etc.) are set to private. Check your security settings. Be careful what information you post online. Once it is on the Internet, it is extremely difficult to remove.
- Encrypt your hard drive and smartphone
- Make stronger password(Check this guide for better stronger passwords: The Key to “Uncrackable” Passwords
- Constantly change your password(i would say 3 months)
- Use a password manager e.g LastPass or Dashlane or KeePass
- NEVER EVER use free Wi-Fi, if you must use a VPN or just dont log in to any site or do online banking.
- For more security tips check out my article on Privacy, Security and Anonymity
- I would suggest you follow an Instagram Page that goes by the name: Bait and Phish
- Search, learn and apply compartmentalization in your life. Separate business, personal etc into compartments.
- Be cautious when giving out personal information such as your name, address, phone number or financial information on the Internet. Make sure that websites are secure (e.g. when making online purchases) or that you’ve enabled privacy settings (e.g. when accessing/using social networking sites).
- Always think before you click on a link or file of unknown origin. Don’t feel pressured by any emails. Check the source of the message. When in doubt, verify the source. Never reply to emails that ask you to verify your information or confirm your user ID or password.
To see real time cyber attacks, go check this site out: https://krebsonsecurity.com/2015/01/whos-attacking-whom-realtime-attack-trackers/
That’s it for today. Have a wonderful day.


4 replies on “Kenya’s Cyber Insecurity”
[…] Kenya’s Cyber Insecurity […]
LikeLike
Hi, I just looked at your website and really impressed by it’s design and information. You are doing an excellent job by providing such information to the people. Thank you so much.
LikeLiked by 1 person
[…] Kenya’s Cyber Insecurity […]
LikeLike
[…] Kenya’s Cyber Insecurity […]
LikeLike